Security Tools to Protect Data-Data security had a challenging year in 2021. A cursory examination of this year’s most significant hacks uncovers some pretty unsettling data and patterns. In addition, malicious actors successfully carried out various specialized cyberattacks and data breaches. As a result, 2021 saw a dramatic rise in cybercrime. The COVID-19 pandemic and corporations’ widespread adoption of work-from-home policies played significant roles in the surge in cybercrime. One research indicated a 600% surge in cybercrime.
Data breaches are becoming more common, as we are all aware. It implies that most individuals are raising their cyber security IQ. Unfortunately, that is not the case! Most individuals are still unsure of key crucially important cyber security subjects, phrases, and concepts.
Here is a summary of four security tools that everyone ought to use to fill in this knowledge gap:
1. Firewalls
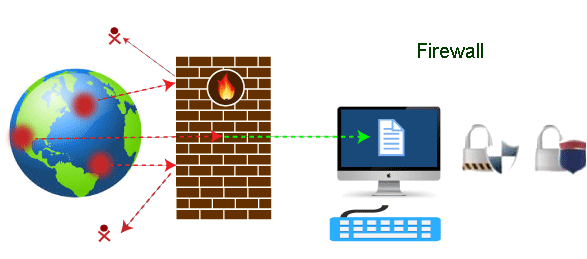
A firewall is the first line of security against viruses, malware, and other dangers (among many others). Both incoming and departing data are scrutinized and filtered. Users can also modify the rules and policies according to their needs. For instance, it’s frequently essential to build exceptions that let specific programmes flow through the firewall so they don’t repeatedly set off false alarms.
2. Antivirus Software
Antivirus software that uses signatures searches files (from any source) for hidden hazards. Additionally, it can frequently quarantine or erase the problematic file if it discovers something suspicious or terrifying. Although antivirus software isn’t infallible, it’s still a crucial component of cyber security, especially regarding zero-day threats (vulnerabilities that hackers discover before software vendors can patch them or users can instal updates). There are numerous options, with costs ranging from nothing to hundreds of dollars annually.
3. Anti-Spyware Software
![10 Best Anti-Spyware Software [Full Analysis 2022]](https://static.safetydetectives.com/wp-content/uploads/2021/08/Best-Anti-Spyware-Software.png)
As the name suggests, spyware discreetly monitors its targets to observe where they go online and, more importantly, what they input, including usernames, passwords, and any other private or confidential information. Anti-spyware software responds to this by (hopefully) identifying and removing dangers like key loggers, password recorders, and other similar tools.
4. Password Management Software
In addition to saving a tonne of time and strengthening security, good password management software also avoids costly errors like saving passwords in web browsers. Here is a review of some common choices if you’re looking for something that will suit your requirements and price range.
Of course, you can also utilize Remote Desktop Manager to safely store your passwords on a centralized platform, along with all your remote connection data and other sensitive information (credit card numbers, etc.). Please request a trial if you’re new to RDM to determine if it’s your best option.
5. Endpoint safety
Endpoint security products use to defend desktops, laptops, and other endpoint devices from viruses, malware, worms, and malicious behaviour. These technologies combine several antivirus programmes with firewalls, antimalware programmes, and other security measures to secure a network for a business.
Conclusion:
For protection against dangers and ambiguity, every firm requires the appropriate security products. Security specialists have introduced various security technologies in recent years to address the threats that hackers pose to a company.
The Security Tools to Protect Data handle some tasks, including identity and access control, endpoint and network protection, cloud security, and network security. These items help an organization’s cybersecurity because they give businesses ways to counter threats.
Also read: What are the Examples of Database use in 2022








GIPHY App Key not set. Please check settings